In our previous article, we looked into The
Domain Name System (DNS) . We found that "www.google.com" actually doesn’t exist !!! What exists is the
IP address. For making it easier for humans to communicate with different web
servers, we established a Domain name system. These DNS servers convert the web
address that we enter in our browsers with it’s corresponding IP address. This
means that whenever we type the address - "google.com", our browsers does’t directly send the request
to google’s server. It first sends the request to the nearby DNS server and
gets the IP address of "google.com"
to which our browser sends the request. This is just a glimpse of DNS . For
reading a whole article on DNS - click here.
 |
| One of my favorite TV Shows-Mr.Robot |
To a hacker,you're just an IP Address. You get hit because you let yourself be an easy mark. It takes just an IP to know everything about you (Metasploit). It's always fun to pick on the nerd...until he has your IP.
So, this is what an IP address looks like...
“ 192.168.1.1 "
>. An IP address is basically a combination
of 4 numbers (These numbers can be represented in 4 Bytes).
>. Each number is of maximum 3 digits lying
in the range from 0 - 255. Basically a binary number of 8 bits at most (from
00000000 to 11111111).
>.Every number is separated by a decimal
point “ . “ .
>.Every IP address is comprised of 2
addresses - “The Network Address” and “The Host Address”. The Network address
of a device implies the network it is connected to. The Host address defines
signifies the device itself.
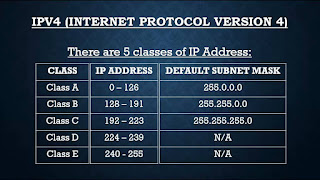
Classification of IP Address:
We now know that the IP Address starts lies between :
0.0.0.0 and 255.255.255.255. On the Basis of the first number (first 4 Bytes) ,
the IP address is classified into 5 Classes.
Class A:
It’s first number lies between 0 and 127 (128
numbers). Therefore the following address can be considered as a Class “A” IP
address:
“ 10.0.0.1 “
As we discussed earlier, that the IP address is
comprised of a Network and a Host ID. For Class A , the network ID is Basically
alloted to the first number only (first 8 bits out of 32). Rest of the bits are
for Hosts.
Therefore the Network ID of the IP address(mentioned
above) is “ 10.0.0.0 “.
To calculate the Network ID from a given IP address,
just put all host bits ‘ 0 ‘ .
The Subnet mask of Class A IP address is 255.0.0.0 .
What’s a subnet mask? We’ll look into it in a minute.
Class B:
An IP Address of Class B has it’s first number from
the range 128 to 191. This is an example of Class B IP Address:-
" 178.168.4.6 "
The first 2 numbers are for the Hosts. Ergo, The
Network ID is 178.168.0.0 (Host bits '0').
The Subnet mask for this class address is 255.255.0.0 .
Class C:
First 3 numbers dedicated to the Network with the
first number in the range of 192 to 233. The Subnet Mask is 255.255.255.0 .
Eg:- "
192.168.1.1 ".
N/W ID:-192.168.1.0
Class D and E are a bit different from the previous
classes. Class D is used for a one to many relation i.e. Multi-casting purposes.
Class E is used for one to one connection i.e. Uni-casting. Both of these aren't
for a particular Host. Therefore there is no need of segmentation of the IP
into Network and Hosts.
Purpose of Subnet Mask :
If you take a closure look at the various class IPv4
addresses and their corresponding Network Addresses, you'll find a connection
between them. All the Host bits are zero. Just by looking at the IPv4 ID can we
compute the Network ID (This is only possible in Classful IP Addresses). This
is how it's done:-
Taking an example of the following IP address : "
192.168.16.5 " We know , by looking at the first number that this address
belongs to Class C. Therefore we know that it's subnet mask is : 255.255.255.0
.
By performing a bit
wise logical AND operation, we get the following result- 192.168.16.0 This is
nothing but the Network ID.
Problem with IPv4
Classful protocol:-
This protocol was a
great way to assign an identification to anyone who wanted a Network. This
Authority of assigning IP's to various organizations was given to The
"Internet Assigned Numbers Authority" (IANA). As soon as this
protocol was accessible to the world, the Numbers filled drastically… There was
scarcity of Address to assign. This was due to Excessive demands and also due
to the wastage of non-utilized IP's . Let's understand the source of the wastage:
Consider a small
organization, which requires 10 Computers for itself. It gives a request to
IANA and gets an IP address : 192.168.5.10 . Since we know that this is a Class
C address. It’s maximum number of Hosts would be 255 . But since this
particular organization would not have more than 10 PC's , 245 locations would
go unutilized. Wastage!
So, to overcome this
problem, we could either increase the number of bytes (IPv6) or Manipulate the
Subnet Mask(Subnetting) .
Anyways, there are
some IP Addresses that cannot be assigned to any of the organizations. Here
they are:-
- 127.0.0.1-This IP address represents the local host. The system itself. From Every computer's point of view, it is the address that points to itself.
- All Host Bits Zero- An address like 192.168.4.0 or 10.0.0.0 or 220.15.0.0 is invalid. As we saw above that this represents the Network ID.
- All Host Bits One- This is known as the Broadcast Address. If in an address, a same request/message is to be sent to all the connected Hosts, we use the Broadcast Address. Hence, an address like 192.168.255.255 cannot be used.
Therefore if A
company/organization wants to setup 5 Hosts in it's Network, 2 extra addresses
are going to be required for Network and Broadcast Purpose. That means 7 total
Addresses.
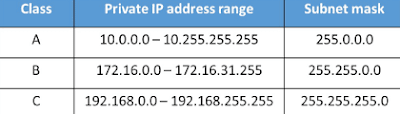
There are also some private IP Addresses for each classes. These IP addresses didn't need any registrations to IANA. Thus, any organization can use it for free. These are the private IP addresses:-
This is why most of you must have seen the IP addresses starting from 192.168 very often.
Classless:
Till now we found
that for each classes we had a fixed Subnet mask that could tell us the number
of Networks and host that can be found in that Class. This was (as we saw
above) a limitation. Therefore, We removed the concept of Classes. This was
done by manipulating the Subnet Mask. In Short, no Classes, no fixed Subnet
masks.
This was the idea:
Taking the same example as before, if an organization asks for 2 PC's to Host.
We would require to provide the Subnet mask which allots 4 places for the
organization (2 for Hosts and 2 Reserved) .We provide an IP address: "
192.168.16.4 ". But now we alter the Subnet Mask from 255.255.255.0 to
255.255.255.252
Let us now check the
Network ID and the requirements.
11000000
. 10101000 . 00010000 . 00000100
(Binary for 192.168.16.4)
11111111 . 11111111 . 11111111 .
11111100 (Binary for 255.255.255.252)
---------------------------------------------------------------------------------------------------------
11000000
. 10101000 . 00010000 . 00000100
(Binary for 192.168.16.4)
N/W
ID- " 192.168.16.4 "
This means the first
computer in this very network would be 192.168.16.4 , 192.168.16.5 ,
192.168.16.6 , 192.168.16.7 (All of these with same N/W ID- 192.168.16.4). As
soon as we try and add another PC into this network and assign the IP address
192.168.16.8, The Network would be changed. Hence, not valid. Don't believe me?
Let's try it out:-
11000000
. 10101000 . 00010000 . 00001000
(Binary for 192.168.16.7)
11111111 . 11111111 . 11111111 .
11111100 (Binary for 255.255.255.252)
---------------------------------------------------------------------------------------------------------
11000000
. 10101000 . 00010000 . 00001000
(Binary for 192.168.16.8)
N/W
ID- " 192.168.16.8 "(Different Network).
Also, We reduced the
Vacancies. But this still does not mean that we are able to decrease the
vacancies by 100%. Therefore a new IP protocol was established. Hence, IPv5 was
made. But that didn't work and was rejected. Finally we gave birth to IPv6
Addressing. I'll be dedicating another article for IPv6. But just to give a
brief idea… IPv6 had more than 4 bytes. Also each byte was separated by a colon
( " : "). The digits entered was Hexadecimal number of 16 bits.
Anyways, This was all about IPv4. I hope you got some idea about what an IP is
and how does it work…
If you want to check your own IP:-
- Goto Run.
- Type cmd and hit enter.
- type " ipconfig ".
I know this concept is a bit tricky. I had a hard time understanding it myself. But it's one of the most Fascinating topics I've ever come across. Need less to say, the inventors of IP Address (Robert Elliot "Bob" Kahn and Vint Cerf) were the "real genius". They made it possible for us to communicate through such long Distances. There is still more to IP. But just so I don't make this article too length, we'll look at it in our upcoming articles.
I hope this helped. Thanks for reading !!! If you have any sorts of doubts, or want me to send a more detailed explanation of the Internet Protocol addressing to your email, please feel free to let me know .
Till then, Keep Exploring !!!