Cicada 3301
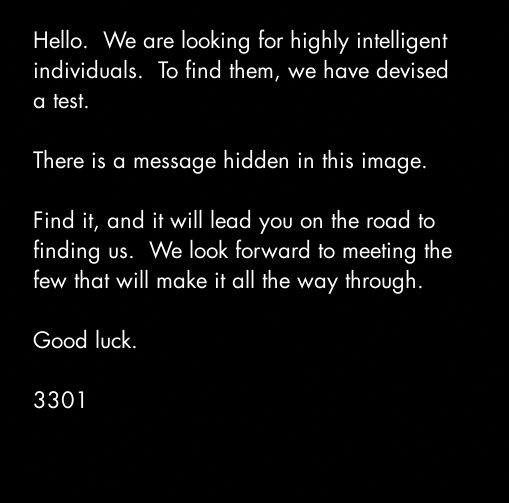
Hello. We are looking for highly intelligent Individuals. To find them, we have devised a test.
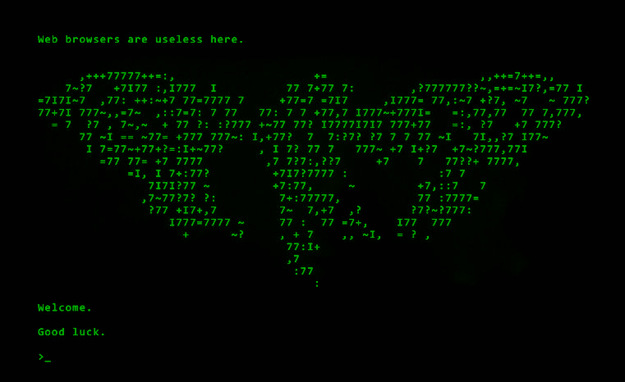
There is a message hidden in this image.
Find it, and it will lead you on the road to finding us.
We look forward to meeting the few that will make it all the way through.
Good luck
3301
This text was posted on 4chan back in 5th Jan 2012. This puzzle caught the eye of the bloggers, experts and cryptologists. It was called "The Cicada 3301".
Clearly this image was trying to tell us something.
Phase 1:
This image was tested by various methods. Some tried to open it through a WinRAR , some altered the brightness levels in Photoshop and observed the noise patterns…until someone found that opening this image through the Notepad, you'll find this text at the Bottom-most line:-
CLAVDIVS CAESAR says "lxxt>33m2mqkyv2gsq3q=w]O2ntk"
This seems to be the famous encryption technique - "Caesar's Cipher"
Caesar's Cipher:-
In this Cipher, the sequential alphabets are shifted by a certain number (In this case by 4).
These are the alphabets written in normal sequence:-
And Caesar's Cipher arranges the alphabets as:-
Shifted by 4 letters.
This ways lxxt>33m2mqkyv2gsq3q=w]O2ntk becomes http://i.imgur.com/m9sYK.jpg .
Phase 2:
Visit the URL!!! DUH!!!
By visiting the URL you'll find this image:-
Phase 3:
Cryptographers often use a Software known as out guess to decode certain messages. Let's give it a try. Here's a link to outguess .
Execute the original image using out guess and we get another URL.
"The Screenshot not shown for Security Issues"
Phase 4:
This time we use the Command Prompt. Another URL. Going to the following URL will lead you to a Book Code.
Phase 5:
We now get a Book Code. There are 83 book codes. This book code is divided into
" page number : word number. "
Phase 6:
Visiting the reddit link we see a page with 188 links. But on the top we see a figure of Morse Code (Lines and Dots). Translating it we get 10 2 14 7 19 6 18 12 7 8 17 0 19 7 14 18 14 19 13 0 1 2 0
Other important field to consider is the Verify note which is basically a PGP key ID. As weird it sounds, it stands for Pretty Good Privacy .
Using a software known as GNU- pg, we can scan anything in Cicada 3301, ruling out the fake ones. On links 121 and 186, we find 2 figures. Again running it through the Out Guess program, we find this particular message:-
Remember the previous key? Convert it to alphabets and we get 2 keys. Using these keys we Go through all the corresponding words, we get this following message:
" Call us at us tele phone numBer two on four three nine oh nine six o "
Calling on this number ,we get this message:
"Very good. You have done well. There are three prime numbers associated with the original final.jpeg image . 3301 is one of them. You will have to find the other two. Multiply all three of these numbers together and add a .com on the end to find the next step. Good Luck . Good Bye!"
The two prime numbers in the original image is basically the dimensions of the image. Multiplying both results together and adding a dot com, we get a count down timer. When this count down was over, there were coordinates of particular locations across the globe. Paris, France, Washington, South Korea and other (in all 14 locations). In all these locations, we find the barcode. Only two of the messages are true. One of them is a poem by William Gibson named Agrippa. When you follow the above book code on this poem, you get "sq6wmgv2zcsrix6t.onion". A Tor URL. Visit the URL and we get message. The other poem is still unsolved.
The last update was a Python Code that on executing will take trillions of years.
Anyways, Cicada 3301 is not yet fully solved. People who are behind this Brilliant Puzzle are assumed to be from another Timeline. Some of the people also claim this puzzle generated by an AI. Remember in our previous article we had a look at the Mariana's Web,the deepest place in an internet... We also talked about the existence of a female Artificial Intelligence. This AI is assumed to control the whole internet. It is also claimed to have generated this Amusing Puzzle.
Another Theory states this puzzle to be an entrance test for MI-7. Anyways, this was the story of the Most Mysterious Puzzle of the Internet. I hope you liked it. If you have any queries or comments you wish to share with me, please feel free. Your comments is the only inspiration that helps me bring such articles to you guys.
Thanks for Reading!